List of sample deployments of Azure App Service with various scenario by using Bicep
- Azure App service with Blob
- Azure App Service + SQLDB + App Insight
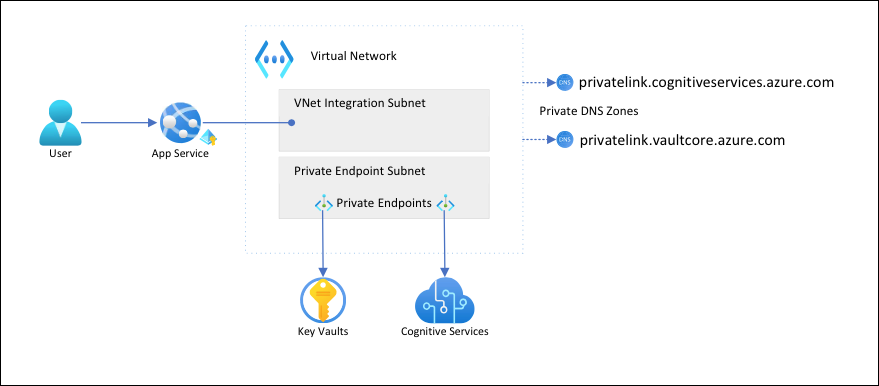
- Azure App Service (Webapp + private endpoint (WebApp and SQL Server) + VNET integration.
- Application Gateway (private and public listeners) -> Azure App Service (via PE) -> SQL Server (via PE)
Azure App service with Blob:
https://github.com/fujute/m18h/blob/master/bicep/00-main.bicep
# https://github.com/fujute/m18h/blob/master/bicep/00-main.bicep RESOURCE_GROUP='21ExampleRG' az group create --name $RESOURCE_GROUP--location westus3 az deployment group create --resource-group $RESOURCE_GROUP --template-file main.bicep --parameters environmentType=nonprod az deployment group list --output table
Azure App Service + SQLDB + App Insight :
https://github.com/fujute/m18h/blob/master/bicep/01-main-web-app-sqldb.bicep
# https://github.com/fujute/m18h/blob/master/bicep/01-main-web-app-sqldb.bicep RESOURCE_GROUP='22ExampleRG' az group create --name $RESOURCE_GROUP --location westus3 az deployment group create --resource-group $RESOURCE_GROUP --template-file 01-main-web-app-sqldb.bicep --parameters sqlAdministratorLogin='azuresqladmin' sqlAdministratorLoginPassword='PLEASECHANGEtoSECRETPASSWORD' location='westus3'
Azure App Service (Webapp + private endpoint (WebApp and SQL Server) + VNET integration:
Deploys two web apps (frontend and backend) and SQL Server securely connected together with VNet integration (webAppFrontend) and Private Endpoint(webAppBackend,SQLServer)
m18h/02-main-webapp-pe-vnet-integration.bicep at master · fujute/m18h (github.com)
# https://github.com/fujute/m18h/blob/master/bicep/02-main-webapp-pe-vnet-integration.bicep RESOURCE_GROUP='23ExampleRG' az group create --name $RESOURCE_GROUP--location westus3 az deployment group create --resource-group $RESOURCE_GROUP--template-file 02-main-webapp-pe-vnet-integration.bicep \ --parameters virtualNetworkName='m6290cvnet' sqlAdministratorLoginPassword='PLEASECHANGETOSECUREPASSWORD'
Reference
Integrate your app with an Azure virtual network
ref:
* https://docs.microsoft.com/en-us/azure/app-service/networking-features
* https://docs.microsoft.com/en-us/azure/app-service/overview-vnet-integration
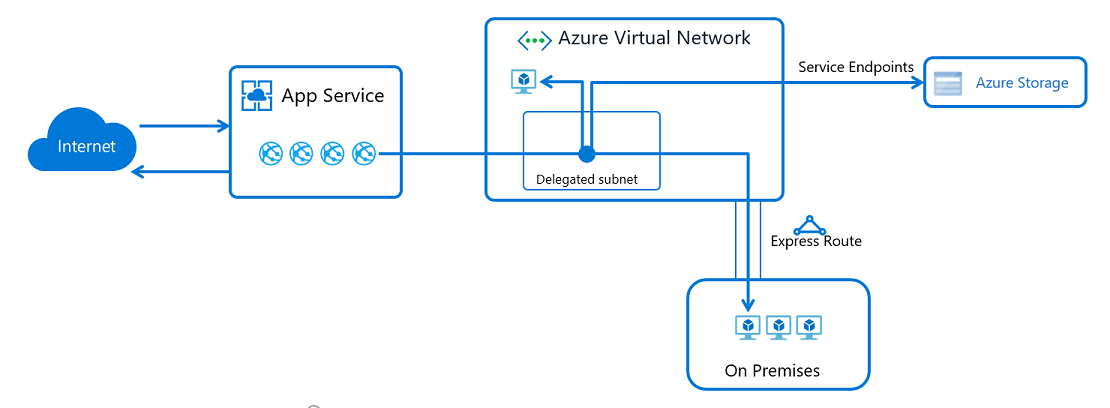
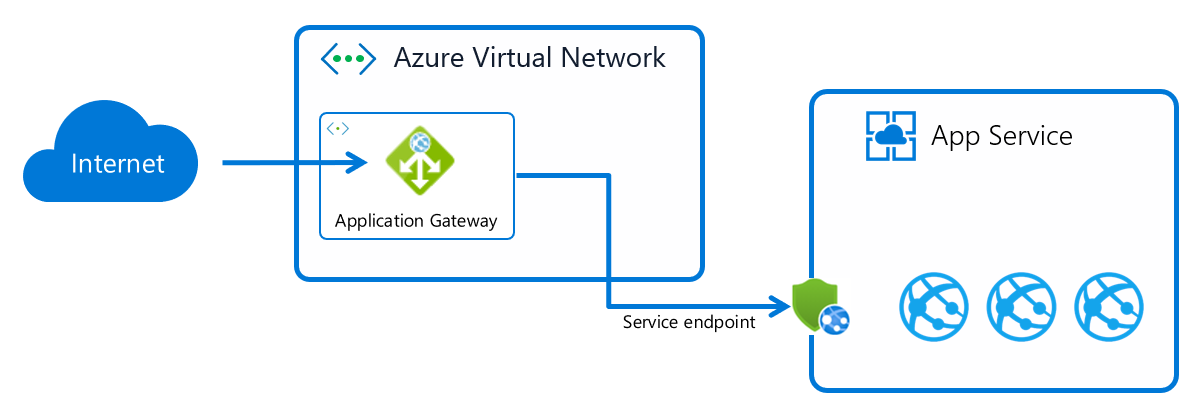
Application Gateway integration: Integration with App Service (multi-tenant)
ref: https://docs.microsoft.com/en-us/azure/app-service/networking/app-gateway-with-service-endpoints
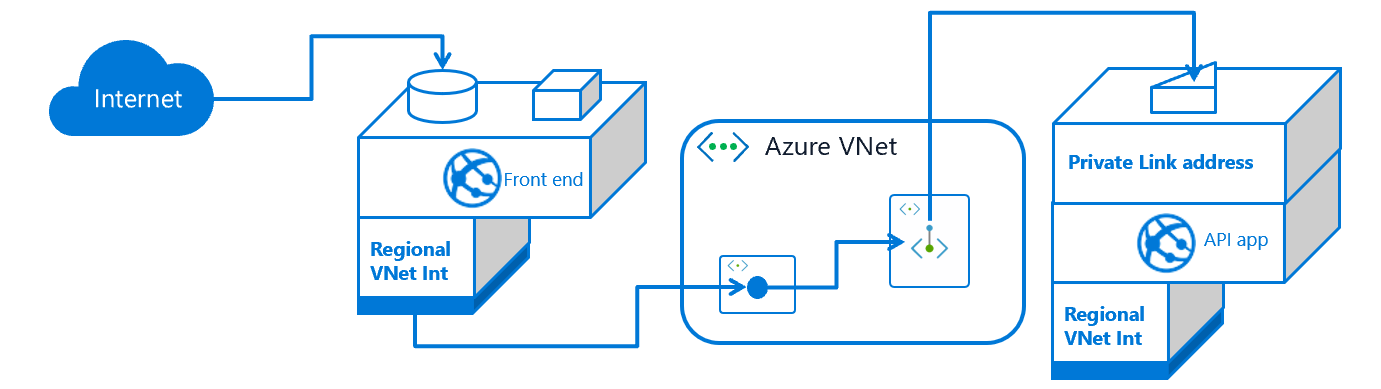
Regional virtual network integration ( multi-tier applications )
Ref: https://docs.microsoft.com/en-us/azure/app-service/networking-features
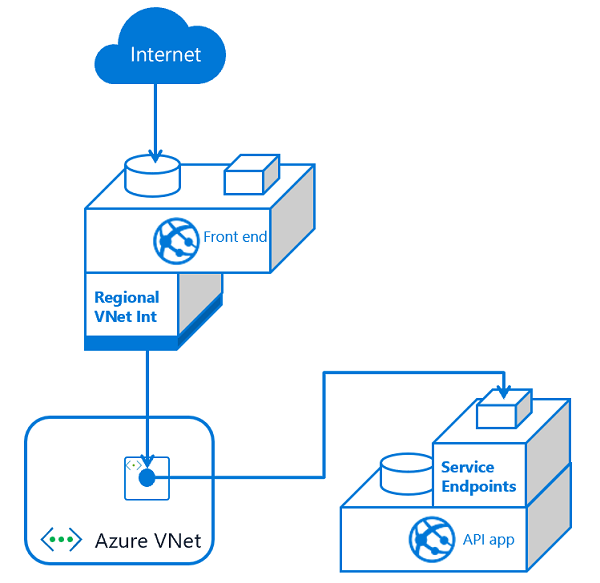
“
*Creating an application gateway with private inbound and outbound addresses.
*Securing inbound traffic to your app with service endpoints.
*Using the virtual network integration feature so the back end of your app is in your virtual network.
..
Configuring private endpoints will expose your apps on a private address, but you’ll need to configure DNS to reach that address from on-premises. To make this configuration work, you’ll need to forward the Azure DNS private zone that contains your private endpoints to your on-premises DNS servers...
This deployment style won’t give you a dedicated address for outbound traffic to the internet or the ability to lock down all outbound traffic from your app. It will give you a much of what you would only otherwise get with an ASE
ref: https://docs.microsoft.com/en-us/azure/app-service/networking-features
“
Tutorial #1
Tutorial: Isolate back-end communication in Azure App Service with Virtual Network integration
Tutorial #2
” Configure v2 custom rules using PowerShell – Azure Web Application Firewall | Microsoft Docs ”
See Also:
- Plan for application delivery: https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/ready/azure-best-practices/plan-for-app-delivery
- https://docs.microsoft.com/en-us/azure/app-service/samples-bicep
- https://docs.microsoft.com/en-us/learn/paths/fundamentals-bicep/
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/bicep/quickstart-create-bicep-use-visual-studio-code?tabs=CLI
- https://docs.microsoft.com/en-us/learn/modules/build-first-bicep-template/4-exercise-define-resources-bicep-template?pivots=cli
- https://docs.microsoft.com/en-us/azure/app-service/tutorial-dotnetcore-sqldb-app
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/bicep/install
- https://docs.microsoft.com/en-us/azure/azure-resource-manager/bicep/deploy-cli
- https://docs.microsoft.com/en-us/azure/templates/microsoft.insights/components?tabs=bicep
Additional information:
https://docs.microsoft.com/en-us/azure/architecture/example-scenario/apps/scalable-apps-performance-modeling-site-reliability
Web app private connectivity to Azure SQL Database
https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/enterprise-integration/ase-high-availability-deployment
https://docs.microsoft.com/en-us/azure/architecture/example-scenario/private-web-app/private-web-app
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/ready/azure-best-practices/plan-for-inbound-and-outbound-internet-connectivity
https://docs.microsoft.com/en-us/azure/architecture/guide/technology-choices/load-balancing-overview
https://docs.microsoft.com/en-us/azure/application-gateway/quick-create-template
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/application-gateway-security-baseline?toc=%2Fazure%2Fapplication-gateway%2Ftoc.json
https://docs.microsoft.com/en-us/azure/application-gateway/configure-web-app?tabs=customdomain%2Cazure-portal
https://docs.microsoft.com/en-us/azure/app-service/app-service-ip-restrictions
https://docs.microsoft.com/th-th/azure/app-service/networking/app-gateway-with-service-endpoints
FAQ:
1.Subnet requirements:
” Because subnet size can’t be changed after assignment, use a subnet that’s large enough to accommodate whatever scale your app might reach. To avoid any issues with subnet capacity, use a “/26″ with 64 addresses. When you’re creating subnets in Azure portal as part of integrating with the virtual network, a minimum size of /27 is required ” More details:
https://docs.microsoft.com/th-th/azure/app-service/overview-vnet-integration
2.App Service ports:
“If you scan App Service, you’ll find several ports that are exposed for inbound connections. There’s no way to block or control access to these ports in the multi-tenant service.” More details: https://docs.microsoft.com/en-us/azure/app-service/networking-features